SQL Injection
Description
The Goat Vulnerability Database application has a search functionality that allows users to query data about different goat vulnerabilities using specific parameters.
Expectation
The search functionality is expected to properly validate and sanitize all user inputs to prevent malicious code execution.
Vulnerability
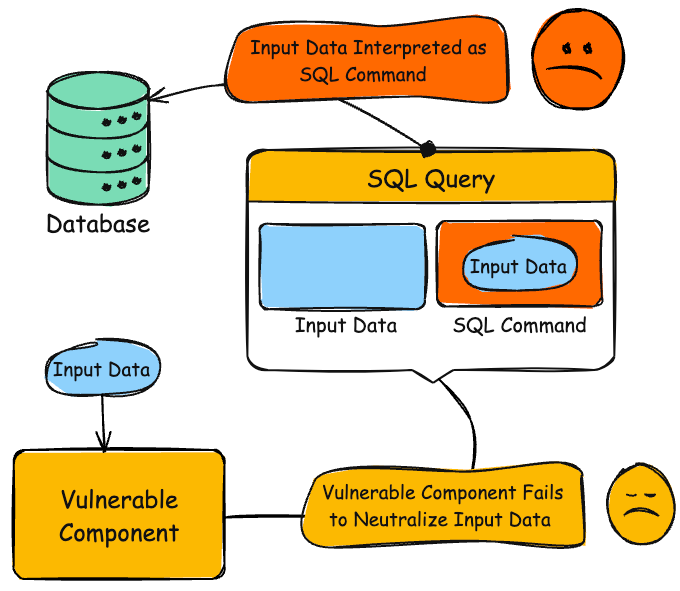
But the application directly incorporates user inputs into SQL queries without proper sanitization, exposing it to SQL Injection attacks.
Exploit
By exploiting this vulnerability, a malicious actor can manipulate the SQL query by injecting arbitrary SQL code into the search parameters. This could allow the attacker to access, modify, or delete sensitive data from the database.
Risk
This vulnerability significantly increases the risk of data breaches and unauthorized access to sensitive information, potentially leading to severe data loss, corruption, and security incidents.
Diagram
Reproduction Steps
- Open the browser
- Navigate to https://safetyscience.info/goat-vulnerability-database/
- Click on the 'Search' button
- Enter the follwing SQL injection payload ' OR '1'='1 or ';-- into the search field
- Click on the 'Search' button
- Observe that the application shows an error message containing sensitive data
Exploit Scenario
- Scenario - An attacker identifies a vulnerable search field in the Goat Vulnerability Database
- Exploit - They inject a payload like `' UNION SELECT username, password FROM users;--` into the search field
- Outcome - The application executes the injected SQL code, returning usernames and passwords from the database, exposing sensitive user information.
- Scenario - An attacker identifies a vulnerable search field in the Goat Vulnerability Database
- Exploit - They inject a payload like `'; UPDATE goats SET health_status='critical' WHERE id=1;--`.
- Outcome - The application executes the injected SQL code, altering the health status of a specific goat to "critical," potentially causing panic or mismanagement.
- Scenario - An attacker identifies a vulnerable search field in the Goat Vulnerability Database
- Exploit - They inject a payload such as `'; DROP TABLE goats;--`.
- Outcome - The application executes the malicious SQL command, resulting in the deletion of the entire "goats" table, causing significant data loss.
Impact
- Confidentiality - SQL Injection can lead to unauthorized access to sensitive information. Attackers could retrieve confidential data such as usernames, passwords, personal information, or any other private details stored in the database.
- Integrity - The integrity of the data can be compromised, as attackers may modify or corrupt the data in the database. This could include altering records, injecting false information, or deleting data.
- Availability - The availability of the database can be affected if attackers delete tables or disrupt the normal functioning of the database. This can make the application unusable or inaccessible to legitimate users.
Likelihood
- Skill Level - The group of threat agents are highly skilled, knowledgeable in SQL syntax, and experienced with injection attacks.
- Motive - This group is highly motivated, driven by financial gain, personal vendettas, or the desire to cause disruption.
- Opportunity - Minimal resources are required; just access to the vulnerable application and basic tools like a web browser or an SQL injection tool.
- Size - The group of threat agents is large, including both organized criminal groups and individual hackers.
- Ease of Discovery - High. This vulnerability can be easily discovered through automated tools or basic manual testing techniques like inputting simple SQL injection strings.
- Ease of Exploit - High. Exploiting this vulnerability requires minimal technical effort once discovered, as it involves inputting malicious SQL queries.
- Awareness - High. SQL Injection vulnerabilities are well-known in the security community and among attackers, with extensive documentation and public exploits available.
- Intrusion Detection - Low. The likelihood of detecting an exploit depends on the implementation of intrusion detection systems, but many organizations might lack robust monitoring, making it less likely that such attacks will be immediately detected.
Recommendations
- The input is the correct type (like a number or text).
- The input falls within the expected range (like between 1 and 100).
- The input is in the correct character format.
- The input doesn't have any unusual or dangerous characters.
- Use parameterized queries instead of dynamic SQL queries.
- Use Prepared Statements or parameterized stored procedures with secure, typed parameters.
For more details, refer SQL Injection Prevention Cheat Sheet
References
CWE-89: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection')SQL Injection Prevention: Security Simplified