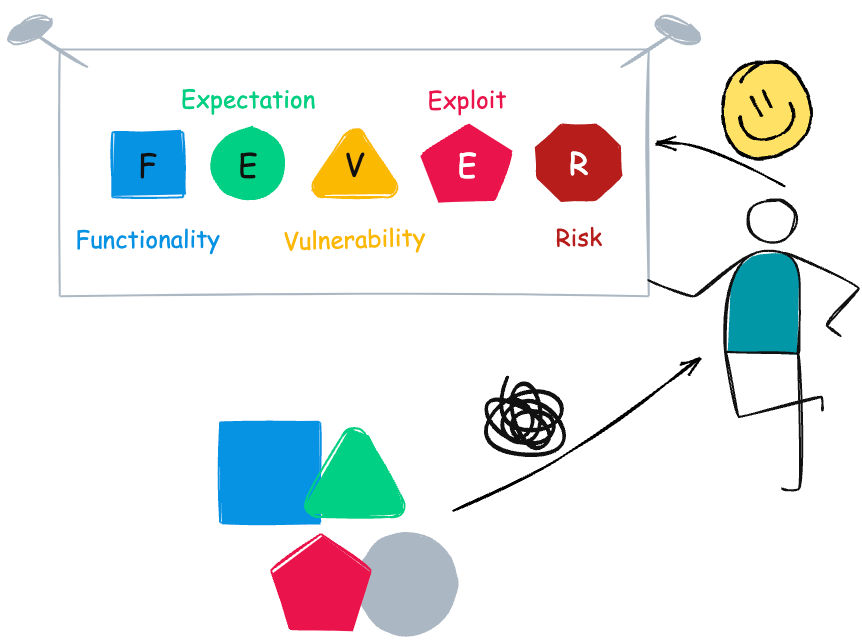
You can use the FEVER method for vulnerability write-ups. Vulnerability write-ups written using FEVER method can be read like stories.
1 - Explain the Functionality
2 - Explain the Expectation
3 - Explain the Vulnerability
4 - Explain the Exploit
5 - Explain the Risk
Example #1
Abracadabra application has change-password functionality which allows the user to change their account-password. The change-password flow is expected to recognize the requesting-user from the session-token or the API key. However, the application uses a user ID parameter to determine the requesting-user. By exploiting this vulnerability, through parameter-tampering, a malicious actor would be able to pass the user-ID of any user in the system and change their password. This vulnerability increases the risk of account-takeover attacks, where a malicious-actor could change and takeover multiple user-accounts in the system.
Example #2
This is a bad example. Please try two write at least a sentence for each element in the FEVER method. If you can't find anything to write for a specific element, skip it. But keep the order to maintain the flow.
Functionality - Login
Expectation - Parameterized queries
Vulnerability - Dynamic queries
Exploit - SQL injection
Risk - Spoofing
Example #3
The profile page of the Abracadabra application lists key account-information including first name, and last name of the user. The profile page is expected to validate and HTML encode the data retrieved from the database. However, the application uses innerHTML property to display the account-information. A malicious user could inject client-side JavaScript injection, also known as cross-site scripting(XSS), payloads on their profile page. All users who visit the malicious actor's profile page will have the malicious actor's JavaScript code running on their browser. Exploitation of this vulnerability increases the risk of phishing attacks. A successful XSS attack allows the attacker to perform all the available actions of the target user in a web application, such as sending messages, capturing keystrokes or conducting financial transactions. XSS scripts may access cookies or session tokens or other sensitive browser data.
Usage
Could you please re-write this using the FEVER method?
Sure! Here is the vulnerability write-up using the FEVER method.
Let's make the FEVER method our baseline for vulnerability description.
This write-up is fine, could you please rearrange the sentences using the FEVER method?

Golden Rules
- Try to use sentences (NOT two words, NOT paragraphs)
- Use a simple language. Refer title
- Reduce the length of sentences
- Stick strictly to description. Don't get into impact, likelihood, reproduction steps, exploit scenario, recommendations, risk ratings, etc.
- Use spell-check and grammar-check
- The flow is important. Stick to the FEVER method to maintain the readability


